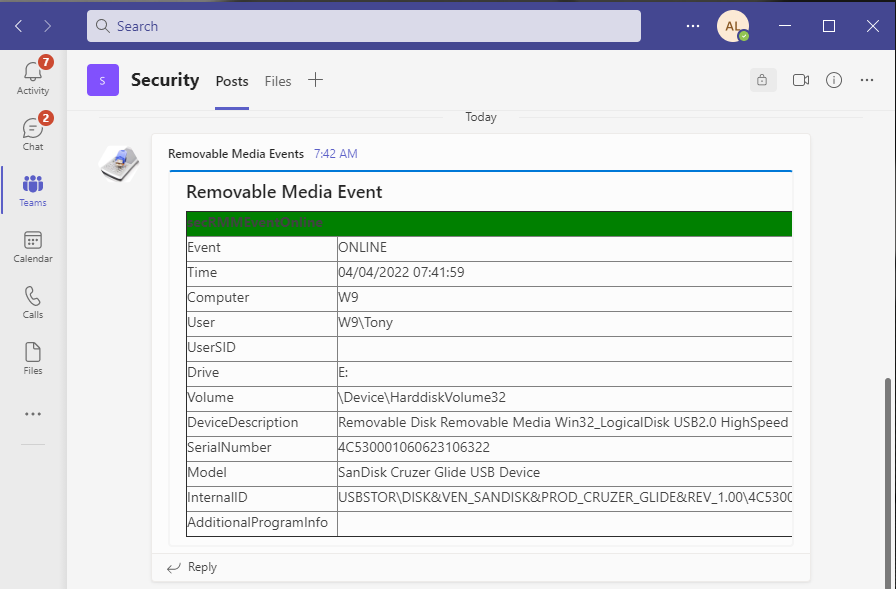
Detailed forensic security data for mobile devices and USB removable storage devices
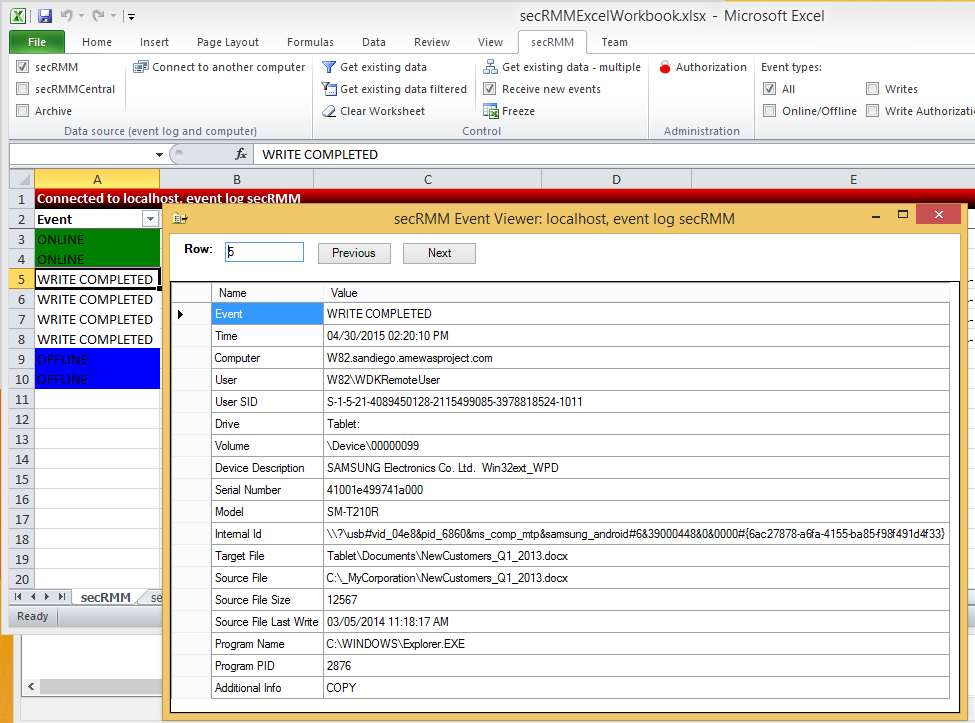 secRMM monitors and collects very detailed forensic security data about removable media write activities.
This ensures that if a security incident does occur and removable media is involved, you will be able to understand the exact nature of the security incident.
The level of detail collected by secRMM is what distinguishes secRMM from other products that attempt to provide similar functionality.
Surprisingly, other competing solutions are not even able to report the files being copied from the local computer and/or network.
Missing this important data makes the security forensic data incomplete and will make any security analysis exercise a guessing game.
secRMM was developed to address requirements coming from the United States government and military organizations.
This means secRMM ensures that removable media write activity is always predictable and the events are always captured to a nonrepudiation store
(i.e. the Windows Security event log).
secRMM monitors and collects very detailed forensic security data about removable media write activities.
This ensures that if a security incident does occur and removable media is involved, you will be able to understand the exact nature of the security incident.
The level of detail collected by secRMM is what distinguishes secRMM from other products that attempt to provide similar functionality.
Surprisingly, other competing solutions are not even able to report the files being copied from the local computer and/or network.
Missing this important data makes the security forensic data incomplete and will make any security analysis exercise a guessing game.
secRMM was developed to address requirements coming from the United States government and military organizations.
This means secRMM ensures that removable media write activity is always predictable and the events are always captured to a nonrepudiation store
(i.e. the Windows Security event log).
Tightly integrated with Microsoft Windows Operating System
 secRMM was designed to fit into the most common security and monitoring scenarios.
This means secRMM utilizes Microsoft best practices by utilizing core Windows Operating System components rather than writing a separate framework to monitor Removable Media devices.
The benefit to this approach is that secRMM does not require a large learning curve or large setup period.
It also means you can integrate secRMM into your existing security and monitoring strategies/implementations with very little work.
secRMM uses the familiar Microsoft Management Console (MMC) as one of its User Interfaces (UI) to make secRMM configuration changes very easy.
secRMM runs on Windows XP through Windows 11 (and all of the equivalent server versions).
secRMM was designed to fit into the most common security and monitoring scenarios.
This means secRMM utilizes Microsoft best practices by utilizing core Windows Operating System components rather than writing a separate framework to monitor Removable Media devices.
The benefit to this approach is that secRMM does not require a large learning curve or large setup period.
It also means you can integrate secRMM into your existing security and monitoring strategies/implementations with very little work.
secRMM uses the familiar Microsoft Management Console (MMC) as one of its User Interfaces (UI) to make secRMM configuration changes very easy.
secRMM runs on Windows XP through Windows 11 (and all of the equivalent server versions).
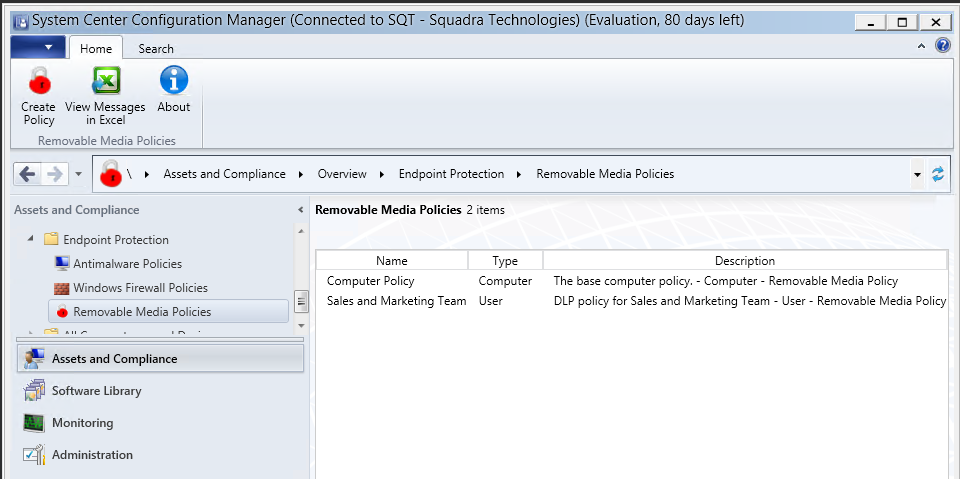
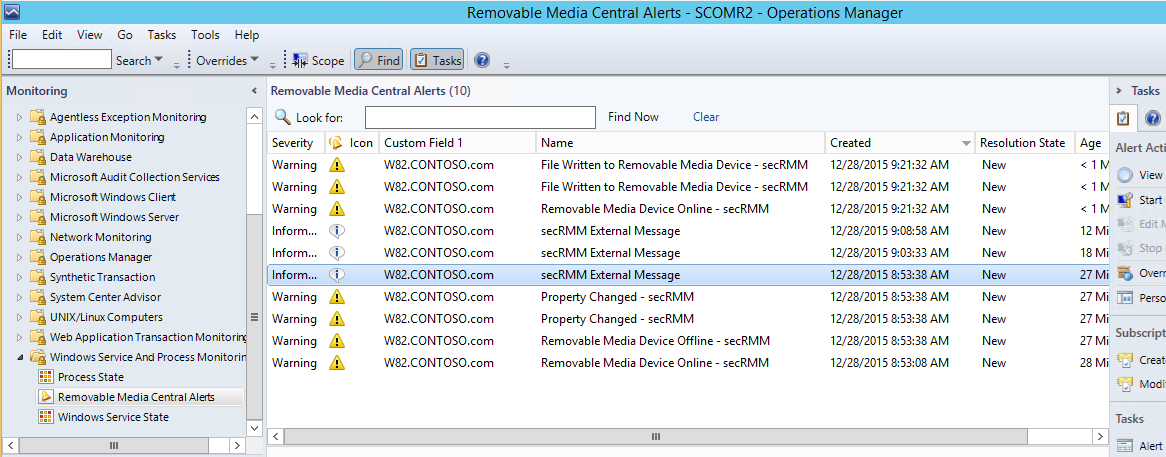
Tightly integrated with Microsoft System Center (ConfigMgr/SCCM, SCOM)
 Watch the SCCM video
Watch the SCOM video
Read the blog
Download
Because secRMM does not use a proprietary framework to function, secRMM easily integrates into the system management tools used within any environment.
Microsoft System Center is the dominant systems management tool on the market today.
secRMM has integration with SCCM, SCOM, Azure Intune, Azure Sentinel and Orchestrator.
For details, please click here.
Watch the SCCM video
Watch the SCOM video
Read the blog
Download
Because secRMM does not use a proprietary framework to function, secRMM easily integrates into the system management tools used within any environment.
Microsoft System Center is the dominant systems management tool on the market today.
secRMM has integration with SCCM, SCOM, Azure Intune, Azure Sentinel and Orchestrator.
For details, please click here.
Tightly integrated with Microsoft Azure Sentinel, Microsoft Defender for Cloud, Azure Monitor
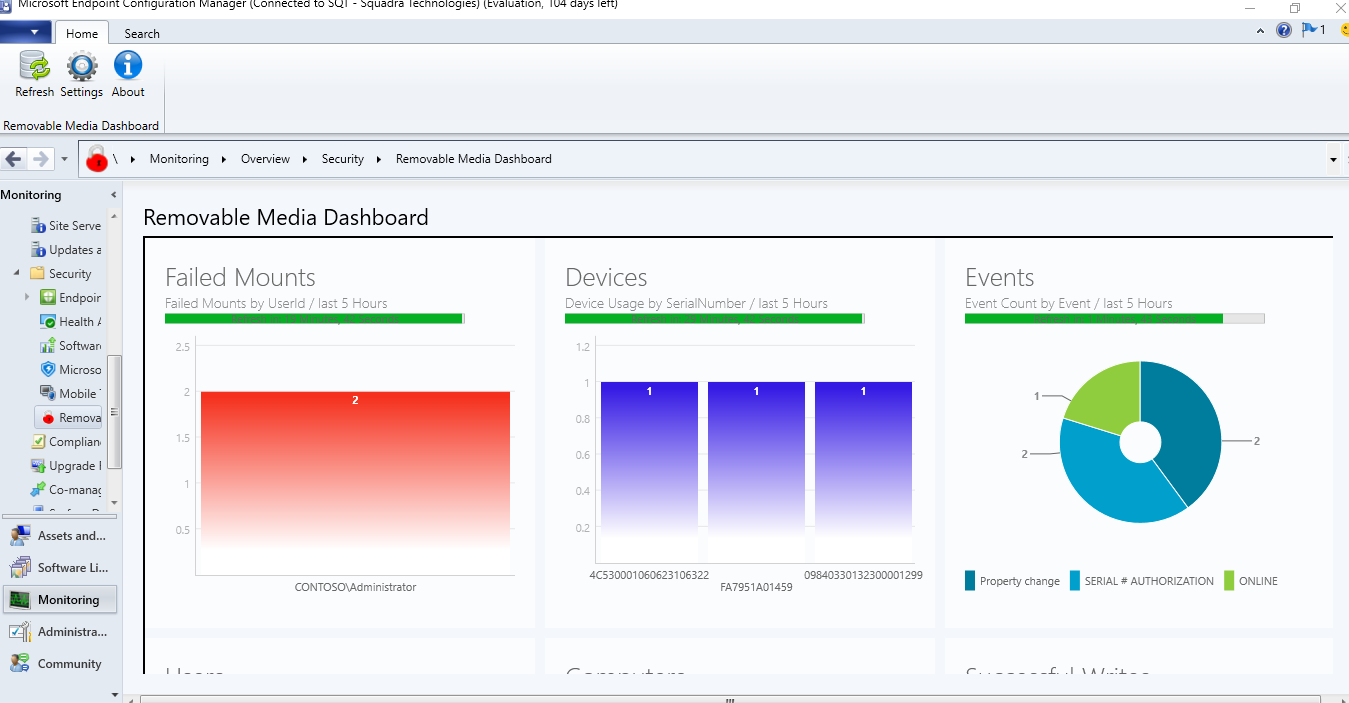
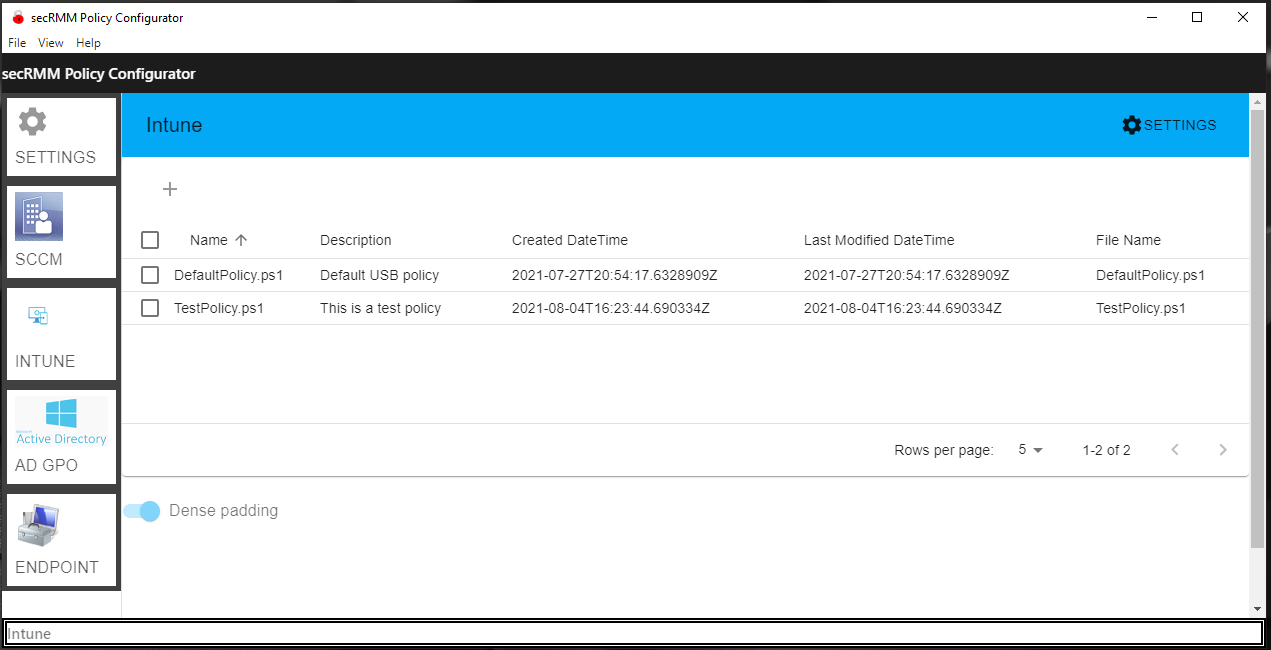
Tightly integrated with Microsoft Endpoint Manager - SCCM/InTune
Watch the video - 1
Read the blog - 1
 Watch the video - 2
Read the blog - 2
Watch the video - 2
Read the blog - 2
 Watch the video - 3
Read the blog - 3
Watch the video - 3
Read the blog - 3
Deploy, configure (device and user policy), report and view dashboards of secRMM security data using Microsoft Endpoint Manager (SCCM/Intune).
When it comes to mobile devices, your MDM framework and your DLP solution should be able to share common data and
set security policy. secRMM has a policy property named "RequireMDMEnrollment" that prevents mobile device mounting
and/or file write blocking if the mobile device is either not MDM enrolled or compliant. You can configure this setting to use either
Microsoft Intune or Microsoft SCCM. Within SCCM, you can also generate meaningful security reports
that show both MDM and DLP events for your mobile devices.
Tightly integrated with Microsoft Rights Management Services (RMS)
Watch the video
Read the blog
secRMM provides integration with Microsoft RMS by providing a security rule named EnableRMS.
The secRMM EnableRMS rule can be set to only allow RMS protected files to be copied to removable storage devices.
You can take it even one step further and have secRMM "RMS protect" files during the copy of the file to removable storage devices.
In both configurations, secRMM logs which RMS template is associated with the file being copied to removable storage.
Tightly integrated with Microsoft Active Directory
 Watch the video
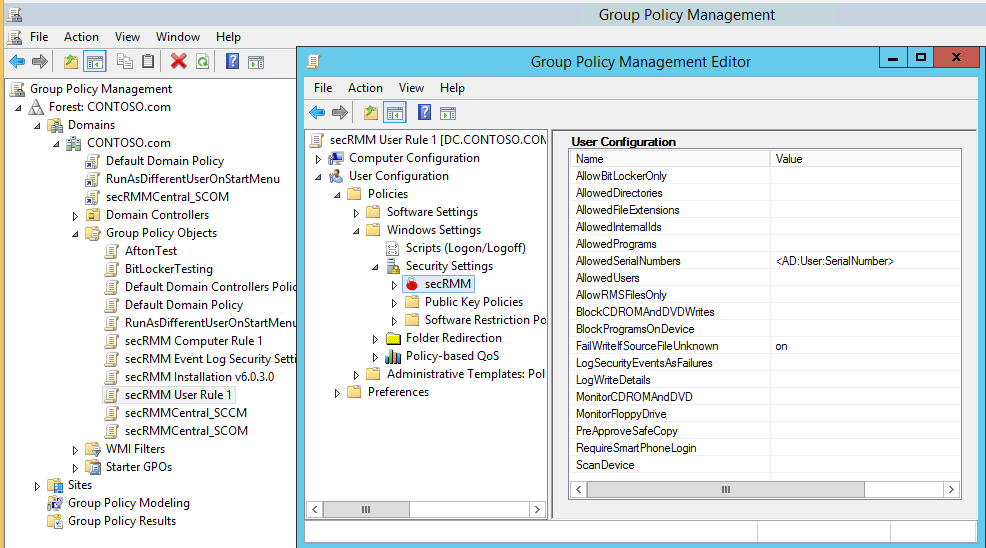
secRMM takes advantage of Active Directory in three powerful ways.
First, secRMM properties can be applied using Active Directory Group Policy.
The Group Policy Editor has both a computer and user configuration security settings secRMM node.
The user interface for the Group Policy Editor is identical to the secRMM user interface in the Computer Management MMC.
This means secRMM security settings can be applied to the computer, a group of users and/or individual users.
Secondly, secRMM can use Active Directory computer object and user object attributes within the secRMM properties (AllowedDirectories, AllowedSerialNumbers and AllowedUsers).
This makes applying removable media security policies very easy to maintain and deploy.
Lastly, you can deploy secRMM and the secRMM license file using GPO software and file copy deployment (please see
Active Directory Installation Guide (PDF) for details).
Watch the video
secRMM takes advantage of Active Directory in three powerful ways.
First, secRMM properties can be applied using Active Directory Group Policy.
The Group Policy Editor has both a computer and user configuration security settings secRMM node.
The user interface for the Group Policy Editor is identical to the secRMM user interface in the Computer Management MMC.
This means secRMM security settings can be applied to the computer, a group of users and/or individual users.
Secondly, secRMM can use Active Directory computer object and user object attributes within the secRMM properties (AllowedDirectories, AllowedSerialNumbers and AllowedUsers).
This makes applying removable media security policies very easy to maintain and deploy.
Lastly, you can deploy secRMM and the secRMM license file using GPO software and file copy deployment (please see
Active Directory Installation Guide (PDF) for details).
Tightly integrated with Microsoft Azure\HyperV\VMware\RDP\RemoteFX
 Watch the video
Read the blog
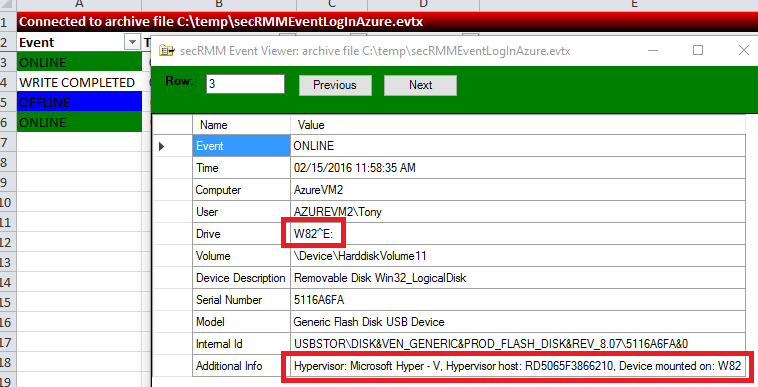
secRMM provides enhanced auditing for Microsoft Cloud and virtual environments.
secRMM supports USB drives that are available to remote machines under Azure and Hyper-V via the
Remote Desktop RemoteFX USB redirection feature. This feature even works when you use a
Remote Desktop session to another physical computer. The secRMM online events contain
information about the Hypervisor server and the remote machine. The event data gets logged
in both the physical and remote secRMM event logs. This gives you a complete picture of
your removable storage within your domain whether it exists on premise or in the cloud.
Watch the video
Read the blog
secRMM provides enhanced auditing for Microsoft Cloud and virtual environments.
secRMM supports USB drives that are available to remote machines under Azure and Hyper-V via the
Remote Desktop RemoteFX USB redirection feature. This feature even works when you use a
Remote Desktop session to another physical computer. The secRMM online events contain
information about the Hypervisor server and the remote machine. The event data gets logged
in both the physical and remote secRMM event logs. This gives you a complete picture of
your removable storage within your domain whether it exists on premise or in the cloud.
Tightly integrated with Microsoft BitLocker
Read the blog
secRMM provides enhanced integration with Microsoft BitLocker.
It allows you to only allow BitLocker encrypted devices within your environment.
secRMM also logs when a device is BitLocker encrypted.
Tightly integrated with Microsoft Scripting languages: Powershell, VBscript, Jscript, CMD
Tightly integrated with Microsoft EndPoint Protection/Defender
Watch the video
Read the blog
secRMM can be set to begin a scan of the removable storage device when it is first mounted.
This is significant because this does not happen by default.
Tightly integrated with Microsoft Excel
 Watch the video
Download
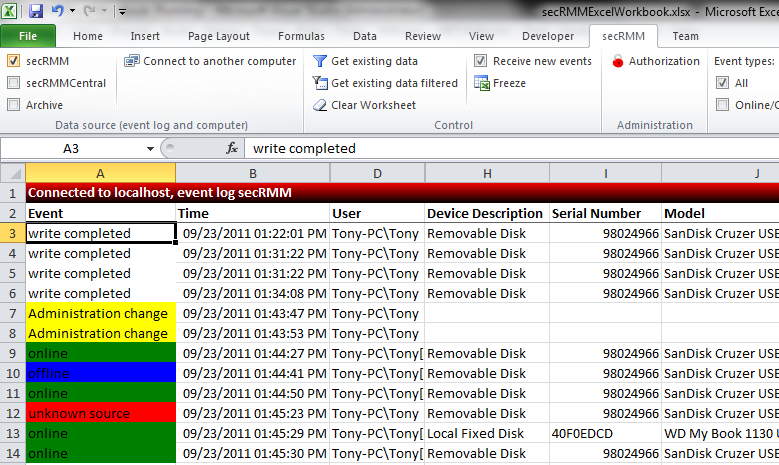
secRMM comes with an Excel AddIn that makes analysis, filtering and reporting of the secRMM forensic security event data very simple.
Watch the video
Download
secRMM comes with an Excel AddIn that makes analysis, filtering and reporting of the secRMM forensic security event data very simple.
Tightly integrated with Microsoft Teams
 Watch the video
secRMM can be configured to send the removable storage security events to your Microsoft Teams which provides near real-time notifications.
Watch the video
secRMM can be configured to send the removable storage security events to your Microsoft Teams which provides near real-time notifications.
Useful yet simple authorization modules
Watch the video
secRMM provides a removable media authorization layer to prevent any removable media security incidents from ever occurring in the first place.
Unlike other competing solutions, secRMM lets you control what files the end-user can copy from the local computer and network.
The other authorization modules let you control removable media write activity based on userid, removable media serial number, removable media internal Ids (i.e. VIDs and/or PIDs)
and the program used to perform the write operations to the removable media.
Prevent unauthorized devices from mounting
Watch the video
secRMM can prevent unauthorized devices from mounting to the Windows Operating System.
The advantage of using this feature is that even though the device cannot be read from or written to, the device still receives power from the Windows computer.
This allows your end-users to still charge their device (usually a smart phone or tablet) while keeping the data in your environment safe.
A corresponding event is generated when this even occurs so you can even know who is charging their phone or tablet.
This feature is available on the device serial number, the device VID/PID and for userids.
Prevent programs, scripts, batch files and office macros from executing
Watch the videos:
programs
,
office macros
Read the blogs:
office macros
secRMM can prevent end-users and "auto-run" from executing various programs types from the removable storage device.
This is one of the easiest ways that malware gets into data centers.
secRMM can prevent this issue and even logs the event so you can educate your end-users.
Transparent integration with hardware/software encryption technology
secRMM works seamlessly with hardware and software encryption technologies.
In fact, secRMM generates the necessary security events required:
1. An event telling you that an encryption device has been plugged into the Windows computer (i.e. mounted)
2. An event telling you that the authorization to use the device has succeeded.
Encryption technology authorization is done using either software (i.e. a dialog asking for your password) or hardware using a push button key pad.
Examples of software authorization include
IronKey devices and
Microsoft BitLocker.
An example of hardware authorization is the
Apricorn Aegis Secure Key USB Flash Drive.
Forward events to System Center (SCCM and/or SCOM), Azure Sentinel, SNMP, Email, Syslog and/or SQL
secRMM generates event data to the local Windows event log.
You will usually want to centralize these events into your enterprise monitoring framework.
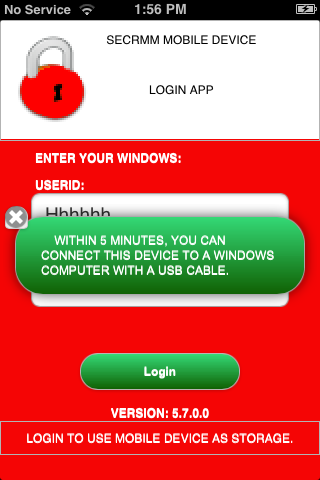
Optional mobile app for added security (authentication)
 Watch the video
Download
For heightened security environments such as military and/or government,
secRMM comes with a mobile app that forces the end-user to login (authenticate)
from the mobile device before the device will appear as a USB storage device to Windows.
Note that you are not required to use this feature; it is an optional security feature.
Watch the video
Download
For heightened security environments such as military and/or government,
secRMM comes with a mobile app that forces the end-user to login (authenticate)
from the mobile device before the device will appear as a USB storage device to Windows.
Note that you are not required to use this feature; it is an optional security feature.
Enforceable two man policy
Watch the video
secRMM comes with an end-user GUI application called SafeCopy that works in conjunction with secRMM.
The SafeCopy user interface mimics the standard Windows explorer program.
However, it only allows writing to removable media and adjusts what it displays to the end-user based on secRMM properties.
Administrators can easily enable secRMM/SafeCopy to enforce a two man policy.
A two man policy means at least 2 people must be involved for the removable media write operation to occur.
The two man policy is a common operating procedure in many critical government and military situations.
The secRMM/SafeCopy two man policy implementation allows administrators to monitor each operation the end-user takes while using the SafeCopy program.
A check is made if an administrator tries to approve himself.
This check will not allow the approval.
Removable Media device tracking
Watch the video
When secRMM writes to any removable storage device, it stores a file that contains tracking data.
An administrator can use this tracking data to determine where the device has been used and what security policies were in effect at the time of the write.
Light-weight
secRMM is designed as a light-weight security software product.
What this means is that when secRMM does not need to be running, it enters into a quiescent state.
The secRMM software will run only when a Removable Media device is plugged into the computer.
This means that your end-users will not feel a performance impact from the secRMM software in their normal day-to-day computer work activities.
Flexible licensing, affordable price
secRMM has 4 different license modes:
1. By Active Directory forest – secRMM provides all features in this licensing mode.
2. By Active Directory domain – secRMM provides all features in this licensing mode.
3. By individual computer – secRMM provides all features in this licensing mode.
4. Freeware – secRMM provides online and offline removable media events only, in addition to unique smart phone and tablet security features.
Please contact our friendly sales team for pricing details.