Why secRMM?
Also, read our Blog...
Straight from the development team
Your boss asks you to find a solution that will help prevent a WIKILEAKS catastrophe in your company or military organization. You head to google or bing, begin your search and are inundated with software security companies that want to help. Many of them are quite well known and you may have the inclination to head to these powerhouses first. But hear us out and please read the rest of this page to let us tell you why we built secRMM the way we did and why we think this software is best suited to monitor the removable media devices in your environment.
How secRMM was built: When we first started designing secRMM, we wanted to answer the question: “What if Microsoft was building such a solution; what would it look like”? One conclusion we arrived at is the product shouldn’t need an entire framework to provide the functionality. In fact, the product functionality should be part of the operating system where possible. Questions around configuration, notifications, reporting and how to render the output data of the product arose. Again, if we were Microsoft, we would make use of the flagship Microsoft systems management product “Microsoft System Center Operations Manager”. Over the last several years, Operations Manager has become the most popular systems management software in the industry and it has configuration hooks, notifications, alerting, reporting (real-time and archival). To be clear, you do not need Operations Manager to use secRMM but if you are using it, secRMM has its own Operations Manager Management Pack which allows you to integrate secRMM into Operations Manager with a couple clicks of the mouse.
You can also configure secRMM to generate SNMP traps (popular among the
enterprise management frameworks). Putting Operations Manager aside, we decided the product should use the event log component for rendering data. We decided to use the Windows Computer Management MMC for the configuration functionality. Both the event log and the MMC come base with the Windows Operating System. Lastly, in addition to providing a configuration user interface via the MMC, secRMM configuration is completely scriptable (vbscript, jscript, powershell, perl, etc.).
What data secRMM captures: Enough about why we built secRMM the way we did. Although we hope you understand now that secRMM does not require a separate framework to implement meaning (for one) that deployment of secRMM is very simple. For all the system administrators reading this, you want to know the nuts-and-bolts of what data gets captured when an end-user or hacker is performing write operations to a Removable Media device. OK, let’s dive in. Below is a subset version of all that is captured. We chose the most important event to cover here. That is, the “Write to Removable Media Event”. If you want to see every detail about the product, please read the secRMM Administrators Guide.
Below is a sample screen shot of a “Write to Removable Media Event”. Below the screen shot, we
will break down the event description text.
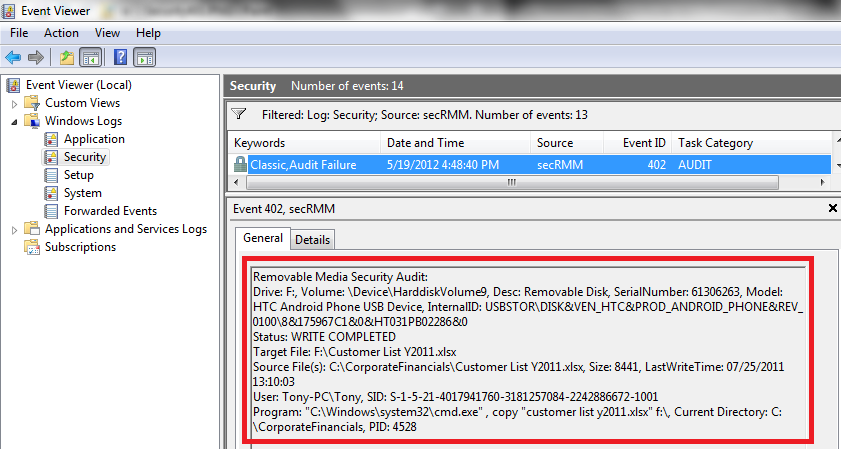
Details
Line 1: Removable Media Security Audit:
Line 2: Drive: F:, Volume: \Device\HarddiskVolume12, Desc: Removable Disk, SerialNumber: 61306263, Model: HTC Android Phone USB Device, InternalID: USBSTOR\DISK&VEN_HTC&PROD_ANDROID_PHONE&REV_0100\8&175967C1&0&HT031PB02286&0
Line 3: Status: WRITE COMPLETED
Line 4: Target File: F:\Customer List Y2011.xlsx
Line 5: Source File(s): C:\CorporateFinancials\Customer List Y2011.xlsx, Size: 8441, LastWriteTime: 07/25/2011 13:10:03
Line 6: User: Tony-PC\Tony, SID: S-1-5-21-4017941760-3181257084-2242886672-1001
Line 7: Program: "C:\Windows\system32\cmd.exe" , copy "customer list y2011.xlsx" f:\, Current Directory: C:\CorporateFinancials, PID: 4528
Line 1 |
Indicates that this event is from secRMM. |
Line 2 |
Describes the Removable Media device.
Listed is the drive letter assigned by the operating system, the volume name, a brief description of the device, the manufacturer assigned serial number, the manufacturer model information and the devices internal ID.
|
Line 3 |
The status of the write operation. This value will be either WRITE STARTED or WRITE COMPLETED. |
Line 4 |
The name of the file that is written to the Removable Media device. |
Line 5 |
The name of the file that is used as input to the write
operation. This file size and liast write time are included. |
Line 6 |
The user that is performing the write operation. The Windows SID is listed in addition to the users Windows name. |
Line 7 |
The program used to perform the write operation. Note that for cmd.exe and explorer.exe, you get additional detail. For cmd.exe, you get the internal command issued (i.e. copy or move) as well as the current directory of the cmd session. For explorer.exe, you get whether the user cut or copied the file(s). |
What makes secRMM unique: In addition to not needing a separate framework, secRMM performs additional analysis when the write operation is performed by either cmd.exe, explorer.exe,
vbscript, jscript and powershell. For a cmd.exe write, secRMM will list the actual command issued (i.e. copy or move) and the current directory of the cmd session. This is true even if you run a 32bit cmd.exe session from a 64bit OS. For an explorer.exe write, secRMM will list the operation (i.e. copy or cut). Why is cmd.exe and explorer.exe important to further analyze? These programs are most likely to be used by end-users and hackers.
What separates secRMM the most from other similar products on the market
today is that secRMM is able to capture the source file(s) that are being
written to the removable media device. While a subtle feature, it is very
significant from a security standpoint. The other products on the market
today only tell you the file name as it resides on the removable media device.
If you are security administrator, what you really want to know is where on the
network or local drives the file came from. secRMM makes removable media
write operations predictable when it comes to capturing the source file.
We strongly believe that these features make us unique from our competitors and the reasons you should consider using secRMM in your environment.
In closing, we hope this article has been helpful in your search for a removable
media security solution.